Last update: $Date: 2025-08-31 16:50:10-06 $
June General Meeting
Google Vision AIY (Artificial Intelligence Yourself) Kit
Speaker: Christian Falkenberg-Andersen

Artificial intelligence, as it relates to vision, will be briefly discussed and the capabilities of the Google vision AIY kit will also be discussed. The implications of artificial intelligence in how it pertains to facial recognition and object detection is something we should all be aware of. Certain countries, like China, have extensive facial recognition systems in place and it is used in many other places as well. There are some scary aspects of computer vision but there certainly are a lot of benefits as well. Some examples will be discussed.
In addition, the code for the Google Vision Kit will be demonstrated. The Kit is a Raspberry Pi Zero-W with a neural network on a device chip (Intel® Movidius™ Myriad™ X VPU). This "Pi Vision HAT" uses the Raspberry Pi Camera version 2 to process live vision and sends the result directly to the Pi. It is a stand-alone product and does not require an internet connection to work.
As a consequence, several powerful programs can be implemented on small physical format sizes (slightly bigger than a deck of cards). During the presentation samples of code, running live, will be demonstrated: including live video emotion detection, recognizing objects, food, and people in video.
Christian Falkenberg-Andersen was born in Denmark and emigrated to Canada at age 14. His parents lived on a farm and solving problems on the farm is likely where an interest in tinkering started. He completed a bachelor of science, majoring in biochemistry (University of Calgary) and taking a course in instrumentation for scientists sparked a very strong interest in electronics. Subsequently he got a second bachelor of science degree (in electrical engineering) and postgraduate master of science degree in biomedical engineering (studying the nerve conduction of a compound action potential traveling down a nerve, and using FFT to calculate the distribution of nerve conduction speeds for the axon). During his work on his master's degree he entered medical school and received a doctor of medicine degree. Subsequently he qualified for practising medicine with specialty in family medicine. He has been working as a solo family physician since 1999 in Market Mall. Currently, outside work activities include a lot of tinkering with the Raspberry PI and Arduino single board computers. Sewing, cycling (electric-assist bike) and kite skiing round out his activities.
Central Library
616 Macleod Trail S.E.Basement meeting room
5:30 PM, Tuesday, June 26, 2018
Snacks at 17:30. CUUG Annual General Meeting begins at 18:00. Presentation begins immediately after AGM.
Attendance is free for CUUG members, or $10 (cash only) at the door for non-CUUG members.
Annual General Meeting and Elections
The Calgary UNIX Users' Group is holding its Annual General Meeting and election of the 2018/2019 Board of Directors. Nominees so far include the following:
Central Library
616 Macleod Trail S.E.Basement meeting room
5:30 PM, Tuesday, June 26, 2018
Snacks at 17:30. Meeting begins at 18:00.
Membership Renewals Due
It is annual renewal time for CUUG memberships. Membership fees remain at
$50.00 (no GST), and cheques can be made payable to Calgary UNIX Users' Group.
Our mailing address is as follows:
Calgary Unix Users' Group
Box 878, Station M
Calgary, Alberta, Canada, T2P 2J6
Invoices have been sent by email. If you have not yet received yours, please contact office at CUUG.
May General Meeting
Home Network Intrusion Detection and Malware Mitigation
Speaker: Greg King, Retired IT infrastructure consultant

There are lots of examples of attacks on companies, governments and public institutions where the attacks went unrecognized for long periods of time. Even organizations practising good IT security hygiene can sometimes fail to notice a harmful intrusion into their IT systems until it is too late. The result can be costly, embarrassing or both. It is not much different for home personal networks. Ransomware, unauthorized crypto mining, identity theft, spyware, and viruses can all impact a home network and can be just as annoying or costly on a personal level by forcing you to change passwords, cancel credit cards, clean infected computers, or legally clean up after identity theft. An intrusion detection system is part of a good home network IT security system which can help to prevent long term exposure to malware and to mitigate the harm. This talk will provide an overview of one of these systems including the setup and demo of an inexpensive home network intrusion detection system.
Greg King has over 40 years experience in computer support from mainframes to PCs and Unix/Linux systems. His most recent experience before retiring was in systems and network monitoring using both commercial and open source monitoring software. Greg is a current CUUG director and continues to dabble in interesting personal IT projects.
Slides from this presentation are available in PDF format.
Central Library
616 Macleod Trail S.E.Basement meeting room
5:30 PM, Tuesday, May 22, 2018
Snacks at 17:30. Meeting begins at 18:00.
Attendance is free for CUUG members, or $10 (cash only) at the door for non-CUUG members.
April General Meeting
IoT Ransomware - We Ain't Seen Nothing Yet (or Have We?)
Speaker: Tom Keenan, Professor, University of Calgary

Ransomware is pervasive, annoying, dangerous and expensive. It has even developed a life cycle from a few ill-chosen clicks to a bunch of encrypted files, ending with a desperate payment in Bitcoin to get them back. Get ready for a new ransomware pattern where nobody does anything wrong or naughty, the target is not files but IoT devices like X-ray machines, and human lives hang in the balance.
Tom Keenan combines a deep technical knowledge with lively insights into the social and cultural aspects of technology. He was educated at Columbia University, receiving BA, M.Sc., MA and Ed.D. degrees in Philosophy, Mathematics, Engineering and Education. He is a popular professor of Environmental Design and Computer Science at the University of Calgary, a Fellow of the Canadian Information Processing Society and the Canadian Defence and Foreign Affairs Institute, and a Research Fellow of the Centre for Military and Strategic Studies. Tom taught Canada's first computer crime course, and was involved in drafting the country's inaugural computer crime legislation.
Dr. Keenan is the author of over 500 academic papers, book chapters, presentations and articles, and has spoken on five continents to academic audiences, major conferences and the general public. His popular book Technocreep dissects how technology is becoming creepy in hidden ways that are difficult for most people to understand. It has appeared in the top ten on Amazon.ca in categories including Civil Rights and Liberties, Technology & Society, and Social Aspects of Technology.
Central Library
616 Macleod Trail S.E.Basement meeting room
5:30 PM, Tuesday, April 24, 2018
Snacks at 17:30. Meeting begins at 18:00.
Attendance is free for CUUG members, or $10 (cash only) at the door for non-CUUG members.
March General Meeting
Thwarting Return Oriented Programming (ROP) Attacks
Speaker: Theo de Raadt, Founder, OpenBSD
In the last two decade various mitigations became popular and the classic "upload code onto stack" buffer overflow attack methods became unreliable or infeasible. These methods were replaced by Return Oriented Programming (ROP).
An ROP attacker gains control of the call stack to hijack program control flow and then executes carefully chosen machine instruction sequences that are already present in the machine's memory, called "gadgets". Each gadget typically ends in a return instruction and is located in a subroutine within the existing program and/or shared library code.
Chained together, these gadgets allow an attacker to perform arbitrary operations on a machine employing defences that thwart simpler attacks.
Some OpenBSD developers are working on a variety of schemes which will thwart ROP by disrupting the foundations it requires.
Please use Google ahead of this talk to lightly familiarize yourselves with "ROP" and "gadgets", and get ready for a low-level deep dive.
Theo de Raadt is widely recognized as a world class security expert. In October 1995, Theo founded the OpenBSD project. OpenBSD is the most secure of the publicly available operating systems.
In 1999, Theo created OpenSSH with other members of OpenBSD. It is now incorporated into all Unix systems plus hundreds of other network enabled products. It has become the most "vendor re-used" piece of open source software, with more than 95% of the SSH market.
Theo was awarded the Free Software Foundation's 2004 Award for the Advancement of Free Software, for recognition as founder and project leader of the OpenBSD and OpenSSH projects. His work has also led to significant contributions to other BSD distributions and GNU/Linux. Of particular note is Theo's work on OpenSSH, his leadership of OpenBSD, his commitment to Free Software and his advancement of network security.
Theo is also well known for his advocacy of free software drivers. He has long been critical of developers of Linux and other free platforms for their tolerance of non-free drivers and acceptance of non-disclosure agreements.
Central Library
616 Macleod Trail S.E.Basement meeting room
5:30 PM, Tuesday, March 27, 2018
Snacks at 17:30. Meeting begins at 18:00.
Attendance is free for CUUG members, or $10 (cash only) at the door for non-CUUG members.
February General Meeting
13 Ways To Break A Firewall, With Live Demonstrations
Speaker: Andrew Ginter, VP Industrial Security, Waterfall Security Solutions

Firewalls are almost always the first technology investment in a new ICS security program, but are they secure? Firewalls have been with us for more than 25 years now — the good guys and bad guys both know how to break through them. Join us to review 13 ways to break through a firewall, each with between dozens and thousands of examples in the wild. Time permitting, up to five of these techniques will be demonstrated live, on a modern, next-gen firewall. This presentation also reviews seven compensating measures deployed routinely to address firewall vulnerabilities on control system networks, and evaluates each measure against each of the 13 classes of attacks.
Andrew Ginter is the VP Industrial Security at Waterfall Security Solutions and an Assistant Professor at Michigan Technological University. Before Waterfall he led teams developing SCADA system, IT/OT middleware and SCADA security products for a variety of vendors. At Waterfall Andrew leads a team responsible for outreach to schools, standards bodies and industrial control system security practitioners. Andrew is the co-author of the Industrial Internet Consortium's Security Framework, the author of "SCADA Security - What's broken and how to fix it," the co-chair of the ISA SP-99 security technology workgroup, and a frequent writer and speaker on control system security topics. He holds B.Sc. AMAT and M.Sc. CPSC degrees from the University of Calgary, and is located in Calgary, Alberta.
Central Library
616 Macleod Trail S.E.Basement meeting room
5:30 PM, Tuesday, February 27, 2018
Snacks at 17:30. Meeting begins at 18:00.
Attendance is free for CUUG members, or $10 (cash only) at the door for non-CUUG members.
January General Meeting
Designing and Building Printed Circuit Boards on a Shoestring Budget
Speaker: Chuck Rohs, Endpoint Security Developer, Cisco Systems, Inc.
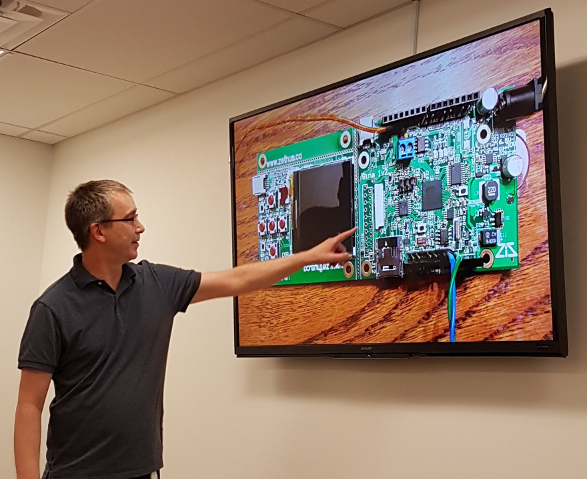
Many people like to tinker with development boards — e.g., Arduino, Raspberry Pi, BeagleBoard, ODROID, ESP8266, etc. — or build electronic projects from discrete components. Frequently these projects end up being a rat's nest of wires on a breadboard. What many people don't realize is that designing and building a printed circuit board (PCB) is easily within the reach of the hobbyist, with a few simple tools. Developing a PCB can sometimes be easier than prototyping, allows for a more robust mechanically stable project, and the possibility of easily making multiple boards for family or friends.
This discussion will illustrate the steps involved in printed circuit board design and manufacturing at the hobbyist level by reverse engineering a Raspberry Pi Amplifier "HAT". This discussion will cover:
- Board inspection for reverse engineering
- Component determination
- Examination of reference designs of key parts
- Schematic capture (in Protel)
- Bill of materials
- Footprint generation
- Board fabrication (DirtyPCBs)
- Board paste-up and reflow
- Tools required
Chuck Rohs is an endpoint security developer at Cisco Systems, Inc. Chuck has a background in embedded software development and security, and was a founder of Au-Zone Technologies Inc.
Central Library
616 Macleod Trail S.E.Basement meeting room
5:30 PM, Tuesday, January 23, 2018
Note that this is the fourth Tuesday of January (not the last Tuesday).Snacks at 17:30. Meeting begins at 18:00.
Attendance is free for CUUG members, or $10 (cash only) at the door for non-CUUG members.

Following Chuck's presentation, Christian Falkenberg-Andersen demonstrated an assembled do-it-yourself artificial intelligence voice kit for performing natural language recognition and connecting to the Google Assistant. Relevant links include the following:
- Google AIY Voice Kit
- ordering from ModMyPi
- MagPi article which first introduced the kit
- Christian's source code (contains some known bugs)


December Holiday Social
CUUG December Holiday Season Social Evening
It's December, and in keeping with our tradition of recent years, CUUG members and their invited guests will get together for a social evening at the Regency Palace restaurant on Tuesday, December 12, 2017. We'll have a private room and have food from the buffet. Attendees pay for their own drinks.
If you are a CUUG member and would like to join us, please e-mail office at cuug.ab.ca so that we can get a good count of how many people to expect. If you would like to bring a guest, please let us know your guest's name as well.
We look forward to seeing you there!
Regency Palace Restaurant
335 - 328 Centre Street South5:45 PM, Tuesday, December 12, 2017
This event is for CUUG members and invited guests.



November General Meeting
How To Train Your Modern C++ Dragon: A Guided Tour in The Zoo of Wild Language Constructs
Speaker: Dr. Thierry Lavoie, Ph.D., Manager - Static Analysis Technologies (SAT), Synopsys

Welcome to the wonderful zoo that is C++! Known to be closer to a federation of languages than a single language, C++ is a complex beast mystifying the most seasoned of software engineers. However, 35 years into the making, it is still a cornerstone of software engineering. How to find our way among the wild constructs, between the old and the new, without leaving a leg to the alligator?
The answer is simple: by taking a tour and exploring the language yourself! Metaphors aside, the goal of this talk is to provide an overview of C++ with emphasis on the modern features of the language and how to adopt the latest common practices. We will look at some of the defining features of C++, like templates, but will focus on the latest additions, like move semantics and r-value references, compile-time type inference, lambdas, const expressions, changes to memory management, and even some of the experimental features, like concepts and modules. To understand how they belong in the large federation that is C++, we will look at all its major eras: pre-ISO, C++03, C++11, C++14, C++17, and the still being designed C++20.
Dr. Thierry Lavoie is a former senior engineer turned manager in the static analysis group at Synopsys. He holds a Master's degree and a Ph.D. in static analysis from the University of Montreal, where he also lectured on compilers and data structures for several years. He is currently the principal voter on the ISO C++ Standard Committee for Synopsys. He has implemented parsers for PHP and Java, as well as island-parsers for C and C++.
Slides from this presentation are available in PowerPoint format.
Central Library
616 Macleod Trail S.E.Basement meeting room
5:30 PM, Tuesday, November 28, 2017
Snacks at 17:30. Meeting begins at 18:00.
Attendance is free for CUUG members, or $10 (cash only) at the door for non-CUUG members.
October General Meeting
Public Key Infrastructure
Speaker: Fady Bashay, Senior Security Consultant, Paladion Cyber Security Experts
The way business evolves every day shows an increasing demand for more secure email, web access, and Virtual Private Networks (VPN). Public Key Infrastructure (PKI) is the most preferable and strong security technology that provides identification, authentication, and encryption to most organizations.
We will explore the two well known ways of encryption: the Symmetric Key and Public Key. Then we will examine the top concerns that CISO's have today with respect to the use of certificates. What are the best practices that organizations should adopt for proper certificate management.
Fady Bashay is a Security Consultant who specializes in PKI, Certificate lifecycle management, cryptography and key management. He has a Master of Engineering Information System Security from Concordia University in Montreal and is currently working at Paladion Inc. as Senior Security Consultant.
Central Library
616 Macleod Trail S.E.Basement meeting room
5:30 PM, Tuesday, October 24, 2017
Snacks at 17:30. Meeting begins at 18:00.
Attendance is free for CUUG members, or $10 (cash only) at the door for non-CUUG members.
September General Meeting
Building a Dumb Web Server, and Why That Can Be a Smart Thing to Do
Speaker: Alan Dewar, President, Calgary UNIX Users' Group

As more and more aspects of our lives develop an on-line presence, web servers become correspondingly more sophisticated to deal with the increased demands for shiny new functionalities. It can be tempting to install the latest and greatest web server so that you, too, can show off to the world. Unfortunately, the latest and greatest soon become old and unsupported, leaving you potentially vulnerable to remote exploits. Thus, it is essential to keep your web server up to date with the latest security patches.
Or, you could take the opposite approach. If all you really need is to serve static content, that's easy! Instead of running the most configurable and high-powered web server you can find, dumb things down and go with an absolutely minimal web server that only knows how to do the most trivial things. The less there is to your server, the fewer things can go wrong.
Alan Dewar describes the anatomy of an HTTP conversation between a browser and a web server, and shows how simple it can be to implement a dumb server to support this. There are a few things you need to be careful about, but once these are addressed, your web server should never need upgrading. It won't provide all the new bells and whistles of more sophisticated web servers, but if those aren't a requirement for you, then you can rest easy, knowing that your web server is too stupid to be hackable.
Alan Dewar is a long-time CUUG member and current CUUG President. He has a Master's degree in Computer Science and develops software for a living. He has implemented simple web-serving functionality in the course of previous employment, and more recently at CUUG.
Slides from this presentation are available in PowerPoint and PDF format.
Central Library
616 Macleod Trail S.E.Basement meeting room
5:30 PM, Tuesday, September 26, 2017
Snacks at 17:30. Meeting begins at 18:00.
Attendance is free for CUUG members, or $10 (cash only) at the door for non-CUUG members.
2017 Board of Directors
At the June 2017 Annual General Meeting, the following people were elected to the Board of Directors for 2017/2018:
- Alan Dewar (President)
- John Clarke (Secretary-Treasurer)
- Neil Glenn
- Greg King
- Winson Duong